The UK Further and Higher Education sectors are increasingly becoming targets for cyber-attacks. These attacks range from opportunistic ransomware operations to more sophisticated Advanced Persistent Threat (APT) groups. This report provides a comprehensive overview of the current cyber threat landscape facing these sectors, recent attacks, upcoming cyber security events, and practical tips for improving cyber security.
Current Threat Landscape
According to the Cyber Security Breaches Survey 2022, 39% of educational institutions identified at least one breach or attack in the last 12 months. The 2023 edition of the survey further highlights that all types of education institutions are more likely to have identified cyber security breaches or attacks in the last 12 months than the average UK business.
Types of Threats
The most common types of breaches experienced by educational institutions are phishing attacks (83%), followed by impersonation (27%), and viruses or other malware (26%). These threats pose significant risks to the integrity of institutional data and the privacy of students and staff.
Impact of Threats
The impact of these breaches on educational institutions is substantial. The 2022 survey reports that 35% of educational institutions that identified breaches experienced a negative outcome, such as loss of access to services or data. This highlights the potential consequences of cyber threats and the importance of robust cyber security measures.
Cyber Crime in Education
The 2023 survey provides specific data on the prevalence of cyber crime in educational institutions. It states that around half of further and higher education institutions have experienced any cyber crime in the last 12 months. This alarming statistic underscores the seriousness of cyber crime in the education sector.
Cyber Security Measures
Around half of further and higher education institutions have a cyber security strategy in place, according to the 2023 survey. This is a positive step towards combating cyber threats, but there is still room for improvement. The survey suggests that these institutions have started to move towards more proactive cyber security approaches in recent years.
Recent Attacks
2020: Rise in Cyber Attacks
In 2020, the UK’s higher and further education sectors experienced a significant number of cyber attacks. According to a survey by TopLine Comms, 33% of the educational sector acknowledged being a victim of cyber-attacks in that year, with 45% refusing to provide any details about the attacks. The National Cyber Security Centre (NCSC) launched an investigation into these attacks but did not confirm whether they were linked.
A survey conducted by the Department for Science, Innovation and Technology (DSIT) between September and January revealed that 85% of 52 higher education providers identified breaches or attacks within the past 12 months. Higher education institutions were more likely to be targeted than any other form of education body, and more than other sectors, with just 32% of UK businesses reporting attacks in the 2023 survey. Half of the higher education institutions that identified breaches reported experiencing attacks at least weekly.
Jisc’s sixth annual survey of the sector, carried out in June 2022, showed that almost all (97%) of higher education and 94% of further education providers have cyber security on their risk register. High numbers also regularly report on cyber risks and resilience to their executive board; 87% of HE and 79% of FE organisations. In 2020, there were 15 serious ransomware attacks on HE and FE providers in the UK.
The major cause of such attacks is “phishing” and “lack of cyber awareness training” where users are targeted with a malicious link to gain access to their account and move laterally within the infrastructure to further disrupt the network and deploy the malware on the end-user devices 1.
2021: Continued Rise in Cyber Attacks
In 2021, cyber attacks continued to rise, with ransomware attacks becoming more sophisticated and disruptive. The education sector was the most targeted by ransomware attacks, accounting for 44% of all attacks in the sector. The UK government launched a new initiative to help schools and colleges recover from cyber attacks. The Cyber Security Breaches Survey 2021 reported that 39% of businesses and 26% of charities experienced a cyber security breach or attack in the last 12 months. The education sector was not separately reported.
2022: Increasing Sophistication of Attacks
The Cyber Security Breaches Survey 2022 reported that 41% of primary schools, 70% of secondary schools, 88% of further education colleges, and 92% of higher education institutions identified breaches or attacks. The most common types of attacks were phishing and impersonation attacks. Higher education institutions were more likely to identify a wider range of attacks, including viruses, spyware, malware, and unauthorized accessing of files. Higher education institutions were more severely affected by breaches or attacks, with 62% reporting experiencing breaches or attacks at least weekly and 71% experiencing a negative outcome, such as a loss of money or data. Almost all educational institutions reported that cyber security is a high priority for their senior management.
2023 (up to July): Persistent Threats and Growing Recognition of Cyber Security
The trend of increasing cyber attacks on educational institutions continues. The education sector is still struggling with cyber security, with many institutions lacking the necessary resources and expertise to effectively protect against and respond to cyber attacks. There is a growing recognition of the importance of cyber security in the education sector, with more institutions implementing cyber security measures and providing training for staff. The UK government continues to provide support and guidance to educational institutions to improve their cyber security.
Threat Spotlight: QR Code Phishing
In the digital age, QR codes have become a common tool for businesses and individuals alike. However, with their increasing usage, they have also become a new avenue for cybercriminals to launch phishing attacks. Here are some recent examples of QR code phishing attempts:
- Fake QR Codes: Criminal hackers have been creating fake QR codes that look legitimate but lead to phishing sites. These codes are designed to trick users into providing their personal information or login credentials (source).

- QR Code Scams: Cybercriminals are exploiting QR codes in a spin on email phishing scams. Scanning these bogus QR codes can lead to phishing attempts (source).
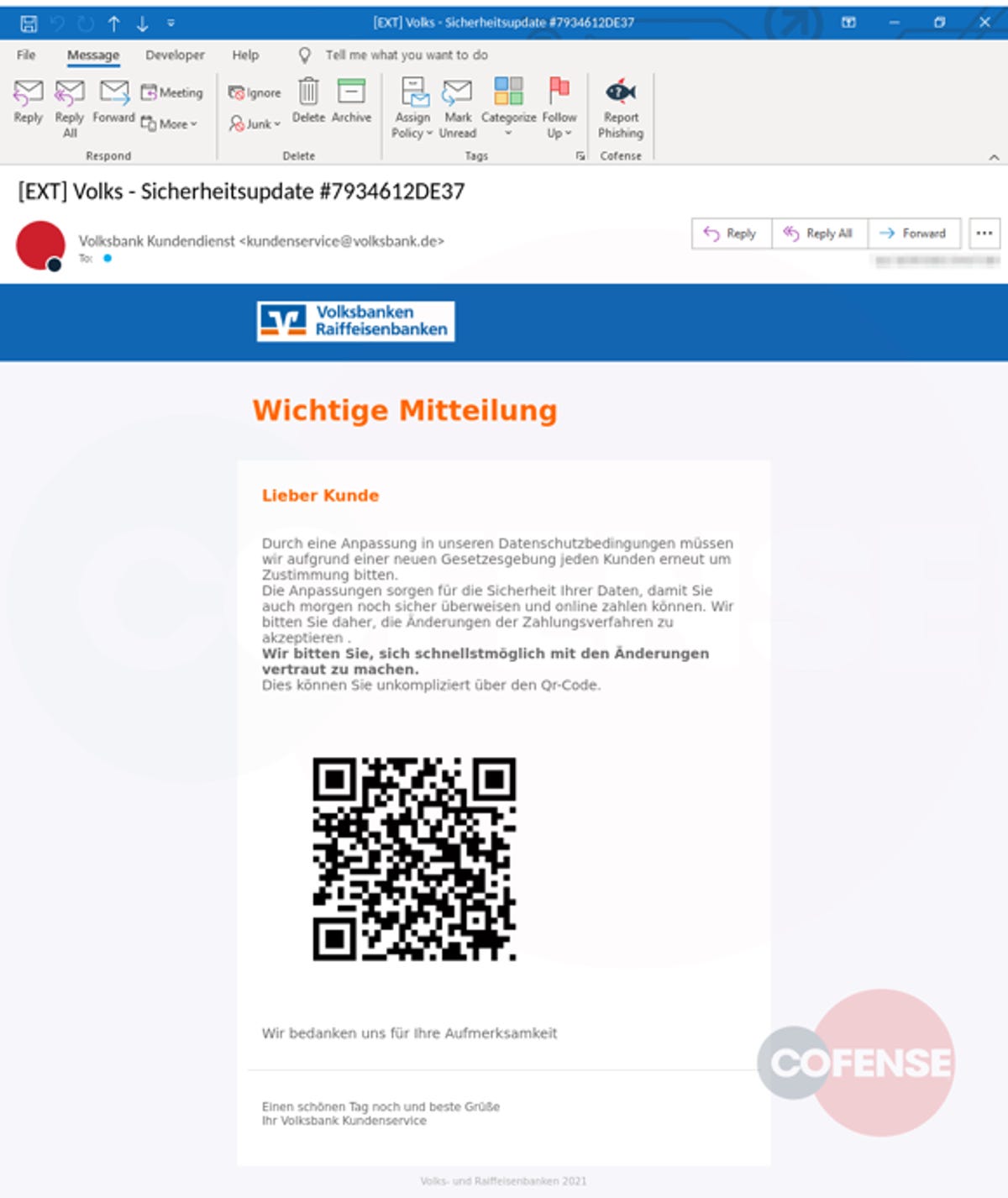
- Targeted Phishing Campaigns: FortiGuard Labs discovered a phishing campaign using a variety of QR codes to target Chinese language users. This highlights the fact that these attacks can be specifically tailored to target certain demographics (source).
- Quishing: A new term coined for QR code phishing, “quishing” involves tricking someone into scanning a QR code with their mobile phone, which then takes the user to a phishing site (source).

These examples underscore the importance of being cautious when scanning QR codes. Always ensure they are from a trusted source to avoid falling victim to these phishing attempts.
Threat Spotlight: Students targeted by bioscience job scams
Recent intelligence reports indicate a surge in cyber threat activity targeting university students with fraudulent job offers in the bioscience sector. These scams are designed to exploit the inexperience of students, many of whom may not be familiar with the tactics used in scams, phishing, and other forms of cybercrime.
Key findings from various sources include:
- Campaigns Using Fraudulent Job Offers: Threat actors have been identified running campaigns that use fraudulent job offers to target university students, particularly in North America. These scams often involve the impersonation of legitimate bioscience, healthcare, and biotechnology companies.
- Extraction of Fees: The primary objective of these scams is financial gain. Victims are often asked to pay a fee in exchange for work. This tactic is particularly effective against students seeking employment opportunities.
- Email Lures: The threat actors typically use email lures, posing as bioscience and health organizations, to entice recipients. These emails often contain attractive job offers, designed to draw in unsuspecting students.
- Intricate Schemes: Some of these scams have been reported to use intricate schemes to target students or potential employees seeking attractive job positions.
Students and university staff are advised to remain vigilant when receiving unsolicited job offers, particularly those that require payment of a fee. It is recommended to verify the legitimacy of any job offer by contacting the company directly through official channels.
MITRE ATT&CK TTPs:
- T1566.001 – Phishing: Spearphishing Attachment: The use of email lures posing as job offers could fall under this TTP. More information can be found on the MITRE website.
Sources:
- “Job Scams Using Bioscience Lures Target Universities”, Proofpoint UK: Link
- “American students bombarded with job scam emails”, Cybernews: Link
- “Hackers Fraudulent Job offers to target university students”, Cyber Security News: Link
- “Job Scams Using Bioscience Lures Target Universities”, Cyware: Link
- “Employment Scams Targeting Students”, University of Washington: Link
Threat Spotlight: Managed File Transfer Solutions
In today’s digital landscape, Managed File Transfer (MFT) solutions are crucial for businesses to securely transfer sensitive data. However, these tools can be vulnerable to exploits if not properly managed and secured. Recent incidents, such as the MOVEit exploits, have highlighted the potential risks associated with these solutions.
Recent Vulnerabilities
Several recent vulnerabilities related to MFT services include:
- CVE-2023-35708: A privilege escalation vulnerability in MOVEit Transfer.
- CVE-2023-34362: A remote code execution vulnerability in MOVEit Transfer.
- CVE-2023-0669: A vulnerability in Fortra GoAnywhere MFT being exploited in the wild.
- CVE-2023-35036, CVE-2023-36934: SQL injection vulnerabilities affecting MOVEit Transfer and MOVEit Cloud.
For a comprehensive list of CVEs, visit the National Vulnerability Database (NVD).
Securing MFT Solutions
Securing your MFT solution involves a combination of best practices, including regular updates and patching, use of encryption, multi-factor authentication, least privilege principle, regular security audits, network segmentation, data retention policies, IP whitelisting, monitoring and anomaly detection, and host isolation.
Known Adversaries
APT28 (Fancy Bear)
APT28, also known as Fancy Bear, is a cyber espionage group believed to be sponsored by the Russian government. They have been active since at least 2007 and have targeted governments, militaries, and security organizations worldwide. The group has been linked to attacks on the Democratic National Committee (DNC) in the United States and the German Parliament, among others.
APT28 is known for its sophisticated tactics, techniques, and procedures (TTPs). They often use spear-phishing emails with malicious attachments or links to compromise their targets. Once they gain access to a network, they move laterally, escalate privileges, and exfiltrate data.
MITRE ATT&CK TTPs associated with APT28 include:
- T1566.001 – Phishing: Spearphishing Attachment
- T1071.001 – Application Layer Protocol: Web Protocols
- [T1059.003 – Command and Scripting Interpreter: Windows Command Shell](https://attack.mitre.org/techniques/T1059/003
Silent Librarian (APT39)
Silent Librarian, also known as APT39, is an Iranian-sponsored APT group that has been active since at least 2013. They primarily target universities and academic institutions to steal intellectual property. The group has targeted universities in more than 30 countries, including the UK.
Silent Librarian uses spear-phishing emails that direct victims to spoofed login pages. Once the victim enters their credentials, the attackers gain access to the victim’s account. They then use these credentials to access other systems and steal data.
MITRE ATT&CK TTPs associated with Silent Librarian include:
Ransomware Operators
The UK education sector has also been targeted by various ransomware operators. These attacks are often opportunistic, with the attackers exploiting known vulnerabilities to gain access to systems, encrypt data, and demand a ransom. In some cases, the attackers also threaten to publish the stolen data if the ransom is not paid.
One of the most notable ransomware strains that has been used against the education sector is Ryuk. Ryuk is often delivered via a multistage attack, with the initial compromise typically achieved through a phishing email containing either a malicious attachment or a link to a malicious website. Once inside the network, the attackers use tools like Emotet and TrickBot to move laterally, escalate privileges, and deploy the Ryuk ransomware.
MITRE ATT&CK TTPs associated with Ryuk include:
- T1566.001 – Phishing: Spearphishing Attachment
- T1071.001 – Application Layer Protocol: Web Protocols
- T1059.003 – Command and Scripting Interpreter: Windows Command Shell
Upcoming Cyber Security Events
Several cyber security events are scheduled for 2023 that may be of interest to the UK Further and Higher Education sectors:
- CyberThreat 2023: This event, organized by the NCSC and SANS Institute, brings together the UK and Europe’s technical cyber security community.
- CYBERUK 2023: This is the NCSC’s flagship event for cyber security professionals in the UK.
- Cyber Series UK 2023: This event focuses on the latest cyber security trends, threats, and strategies.
- Security and Risk Management in Higher Education 2023: This event, organized by Universities UK, focuses on security and risk management in the higher education sector.
Cyber Security Tips
Here are five tips for organizations in the UK Further and Higher Education sectors to improve their cyber security:
- Educate and Train Staff: Cyber security awareness training can help staff recognize and respond appropriately to phishing emails, suspicious activity, and other cyber threats.
- Implement Multi-Factor Authentication (MFA): MFA adds an extra layer of security by requiring users to provide two or more verification factors to gain access to a resource.
- Keep Systems and Software Up-to-Date: Regularly update and patch all systems and software to protect against known vulnerabilities.
- Backup Data Regularly: Regular backups can help recover data in the event of a ransomware attack or data loss.
- Develop an Incident Response Plan: An incident response plan can help manage a cyber security incident by establishing a process to respond and recover.
Regulatory Compliance
In addition to implementing best practices for cyber security, UK higher education institutions must also comply with various regulatory requirements. These include the General Data Protection Regulation (GDPR), which governs the processing of personal data, and the Network and Information Systems (NIS) Regulations, which require organizations to implement appropriate security measures to protect against network and information system incidents.
The NCSC provides a Board Toolkit to help board members understand their legal and regulatory responsibilities for cyber security. The toolkit includes guidance on cyber security regulation and directors’ duties in the UK, as well as practical tips for managing cyber risk at the board level.
Summary
The UK Further and Higher Education sectors face a diverse range of cyber threats, from opportunistic ransomware attacks to targeted operations by APT groups. It’s crucial for these institutions to understand the threat landscape, stay updated on the latest threats, and implement effective cyber security measures to protect their systems and data.
Further Reading
- Almost all UK higher education institutions report cyberattacks
- Cyberattacks target UK universities weekly, survey reveals
- Threat Actor Profile: TA407 (Silent Librarian)
- Ransomware Review: UK
- Seaborgium APT group targets defense, NGOs, think tanks, higher education in NATO countries, especially in US, UK
- The Enduring Cyber Threat to Higher Education: What Next?
- Big Game Hunting with Ryuk: Another Lucrative Targeted Ransomware
- Ransomware in 2023: A SophosLabs Uncut Report
- Cyber Security Standards for Schools and Colleges
- Cyber Security Regulation and Directors’ Duties in the UK
- GDPR Guidance for Higher Educational Institutes
- Cyber Security Breaches Survey 2023: Education Institutions Annex
- Improving the Security of K-12 School Networks
- Mitigating Malware and Ransomware Attacks
- Cyber Security Breaches Survey 2022
- Cyber Security Breaches Survey 2023
